Detect and block exploit attacks against web vulnerabilities announced in OWASP Top 10. Use a validated OWASP CRS ruleset.
WEBCastle
F1–WEBCastle
(Web Application Firewall)
Detect and block hacking attacks against web with server-side agent software and provides a dedicated central management system for efficient management even in large web server environments.
You can use it without any configuration changes as your web server’s throughput increase, because it is not a hardware-based solution.
Even if our solution stops working, your web service will still be connected, because we are
not a way to bypass your web traffic with a cloud service infrastructure.
How it works
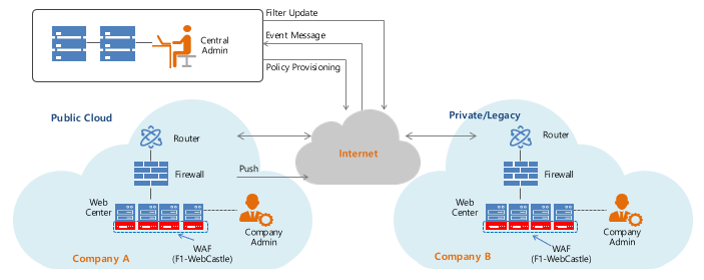
F1Security WEBCastle can be easily installed by downloading the Web Firewall Agent software from an intuitive central management system. WEBCastle provides accurate ruleset-based detection and blocking for OWASP's TOP 10. It can run on existing legacy web servers or virtual machines in the cloud. WEBCastle does not send any web traffic to the cloud, so you can use it without worrying about information leaks from service providers.
Provide essential web application firewall service without interrupting web service

Web hacking protection

Easy installation & setup
Easy installation with no changes to existing network topology, even no need to change DNS servers.
Central management system
Built-in real-time dashboard and report generation. Intuitive UI provides convenience. API interworking function for advanced users.
Seamless scalability
Even with increased web server throughput, you can use the same license fee without any additional cost.

Sustainable web access
If our agent and service platform are stopped, your web service will not be affected. Does not deliberately bypass any of your web traffic.

No leakage due to service.
No web traffic is inspected via the cloud, just is handled inside a server, there is no worry of data leaking through the service provider’s system.
| OWASP Top 10 - 2017 | WEBCastle |
|---|---|
| A1:Injection | |
| A2:Broken Authentication | |
| A3:Sensitive Data Exposure | |
| A4:XML External Entities (XXE) | |
| A5:-Broken Access Control | |
| A6:-Security Misconfiguration | |
| A7:-Cross-Site Scripting (XSS) | |
| A8:-Insecure Deserialization | |
| A9:-Using Components with Known Vulnerabilities | |
| A10:-Insufficient Logging & Monitoring |
Protect the most critical web attacks
Detect and block attacks in real time on the top 10 most critical web application security risks with a validated OWASP CRS ruleset.
Also can apply user-defined-rulesets for your environment.
You can choose the security level of the attack and the blocking policy after detection. Or, simply use the default settings to get effective protection. As the rapid vulnerability attack changes, Managed rulesets are updated regularly by F1Secuity R&D Lab to provide fast and seamless protection against the latest attack.
Click, Use immediately
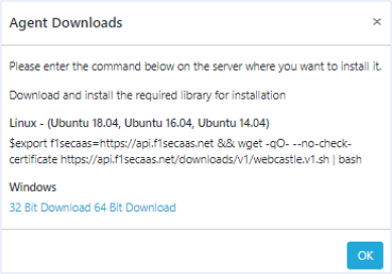
After signing up, you can download the agent software from the management console and install it on your web server and enable web security immediately. No troublesome DNS server changes and no network topology changes for hardware installation.
If you change the DNS server's IP address for a proxy-based web application firewall, the change will take several tens to hours to propagate to the Internet. Our software-based web application firewall can use security features immediately after a few minutes of installation without affecting web service access.
Cloud-based service, But different
We Build, operate, and provide our customers with a central management system in the cloud. But no website access traffic goes through our cloud infrastructure. As a result, our cloud infrastructure failure does not cause any problems for our customers' web services.
Web hacking attack detection and blocking of F1Security WEBCastle is handled inside the web server. Also, for web hacking protection, we do not pass or store any customer web service traffic in our cloud infrastructure, so no web traffic information is leaked from our infrastructure.
Learn more
Reasonable Pricing, Possible
We do not need large-scale cloud infrastructure to bypass and handle access traffic to customer websites, and we do not need dedicated hardware equipment to install customer's network. With the software we developed, everything is solved.
As your web server hardware specifications increase, you can use the same license at no extra cost, even if your web traffic throughput improves. On the other hand, if you use hardware-based WAF appliance, proxy-based SECaaS type WAF services, you can incur significant additional costs.
Learn more